COLLEGE CATALOG DESCRIPTION :
 Survey of concepts and applications of information technology. Introduces role of information technology in solving business problems and supporting organizational functions.
Explores organizational
structure of modern enterprise and role of information technology within this structure. Introduces major components of information technology and its broad applications through various case studies.
Explains need for information technology analyst to understand business-level objectives needed to provide appropriate technology solutions to achieve those goals.
Survey of concepts and applications of information technology. Introduces role of information technology in solving business problems and supporting organizational functions.
Explores organizational
structure of modern enterprise and role of information technology within this structure. Introduces major components of information technology and its broad applications through various case studies.
Explains need for information technology analyst to understand business-level objectives needed to provide appropriate technology solutions to achieve those goals.
Course cannot be applied to
satisfaction of a Liberal Arts and Science elective in any curriculum or of graduation requirements in Computer Science curriculum at SCCC.
COURSE PHILOSOPHY:

This course is required for all three Information Technology tracks.
An understanding of information technology
concepts
is essential for
productive use of computers, networks, and related equipment,
in organizations of all sizes and types.
It is increasingly important to professionals, as well.
This course seeks to give students a thorough, general introduction
to this area
with particular emphasis on organizational and business uses of computers.
Included are introductions to
hardware,
systems software,
applications software,
telecommunications,
networking and the internet,
databases,
security,
and ethical issues.
OBJECTIVES:
After completing this course, the student should be able to:
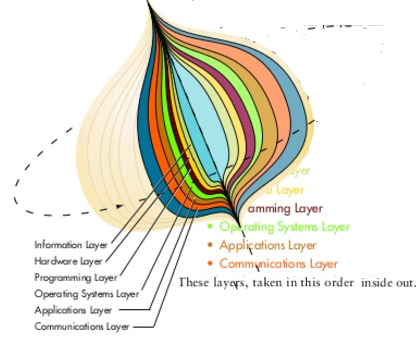
- Recognize and classify information systems encountered in everyday life and in the business world.
- Recognize and define common terms and phrases used in the IT field.
- Understand Internet basics and related hardware & software concepts.
- Be familiar with how each of the following functions:
computer hardware, software, telecommunications, networking, the internet, world wide web.
- Be familiar with the different forms and functions of electronic business,
including
electronic commerce,
electronic document exchange (IDE),
and other forms of business exchanges via internal networks and the internet.
- Be familiar with the ethical issues and choices
associated with the impacts of information technology,
particularly with regard to both privacy and piracy.
- Be familiar with security issues involved in general information technology,
including internet security issues.
STUDENT REQUIREMENTS:
To successfully complete this course, you must submit required homeworks and programming assignmentsts, and demonstrate proficiency on all exams and projects. All work submitted must be neatly
presented clearly labeled and identified as to the assignment and what has been accomplished.
-
TEXTBOOK:
-
 "Computer Science Illuminated"
(4the Edition.)
by Nell Dale & John Lewis
"Computer Science Illuminated"
(4the Edition.)
by Nell Dale & John Lewis
Jones & Bartlett Publishers; ISBM 978-0-7637-7646-6
-
READING ASSIGNMENTS:
-
Each student is responsible for all material taught or assigned by the instructor.
The student is expected to complete all assigned reading, prior to class meetings.

-
OTHER MATERIALS:
-
Flash-stick to save files.
-
COMPUTER & INTERNET ACCESS:
-
 Between classes, the student should have computer access to the internet,
to obtain assignments, submit homeworks and projects, etc.
(NOTE:
If you have ANY difficulty at all in obtaining internet access between classes
please see the instructor after class to remedy this difficulty.)
Between classes, the student should have computer access to the internet,
to obtain assignments, submit homeworks and projects, etc.
(NOTE:
If you have ANY difficulty at all in obtaining internet access between classes
please see the instructor after class to remedy this difficulty.)
COURSE POLICIES:
-
GRADING POLICY:
| Comprehensive final exam: | 40%
|
|---|
| Tests and quizzes: | 40%
|
|---|
| Homework assignments, projects: | 20%
|
|---|
| Participation * | +/- 10%
|
|---|
|
* "Participation" includes: in-class participation,
preparedness, excessive absences, etc.)
|
-
ATTENDANCE POLICY:
Attention is directed to the following statement of college policy.
 "The college expects that each student will exercise personal
responsibility with regard to class attendance. All students are
expected to attend every class session of each course for which they
are registered. Students are responsible for all that transpires in
class whether or not they are in attendance."
"The college expects that each student will exercise personal
responsibility with regard to class attendance. All students are
expected to attend every class session of each course for which they
are registered. Students are responsible for all that transpires in
class whether or not they are in attendance."
|
Consequently, each
student in this course is strongly advised to make standing
arrangements with another individual student to take detailed notes,
collect handouts, relay announcements, etc., in the event 'e doesn't
show up at class. While you are encouraged to contact the instructor
for advice before (or after) missing a class, it is more effective to
have your "buddy" take detailed notes, and the student
remains responsible for "all that transpires in class".
Find a "buddy" to cover for you!
Do it now, not after missing a class.
This instructor does
not give credit for mere attendance, nor is credit lost for absence.
Attendance is not a direct factor in grading policy,
but it may indirectly affect the "participation" component.
College
policy defines "Excessive Absence or Lateness" as
"more than the equivalent of one week of class meetings".
While attendance is not a component of grading policy for this class,
a student missing more than one week of consecutive classes - without
making any contact with the instructor - may be removed from the
class roster and given either a "W" or an "F" grade,
at the instuctor's option.
-
SPECIAL NOTE REGARDING
PROGRAMMING ASSIGNMENTS &
LABORATORY TIME:
In-class
laboratory time is
NOT
intended for students to do most of their work
on the programming assignments and projects; these assignments are to
be done between classes, and are expected to require a minimum of 6
hours per week to complete independently, at your own pace.
Also, please note:
In-class laboratory time is NOT
intended for computer activites unrelated to the college curriculum
(such as games, entertainment, "instant messager", "surfing the web", etc.)
Use of classroom computers for unrelated activities may result in loss of privileges.
-
CODE OF CONDUCT:
*** Please take note ***
|
SCCC STUDENT CODE OF CONDUCT

... Although
not all-inclusive, the following actions, activities or behaviors
are expressly prohibited:
"Unauthorized or illegal use of College computer facilities
or equipment, such as hacking; duplication or unauthorized use of
copyrighted software; destruction, unauthorized transfer or
alteration of files; unauthorized use of another individual's
identification, password or work."
Any
student guilty of the above may receive a failing grade in that
class, be dismissed from class
and/or
be referred to the Dean of Students for further discipline
proceedings.
|
OUTLINE OF TOPICS:
1. The big picture.
Binary values and Numbering systems (part 1).
2. Binary values and Numbering systems (part 2).
Data representation.
(e.g. for integers, rationals and irrationals numbers, etc. as well as
images, sound, structures, etc. Also: compression, encription, error-detection, etc.)
3. The hardware layer.
4. Computing components.
5. Low-level programming languages and pseudocode.
6. Problem solving and Algorithms.
7. Abstract data types and subprograms.
8. Object-Oriented Design and high-level programming languages.
9. Operating systems.
10. File systems and directories.
11. Information systems.
12. Networks, the Internet, and the World Wide Web.
|
B. A. Martin





 "Computer Science Illuminated"
(4the Edition.)
"Computer Science Illuminated"
(4the Edition.)

 Between classes, the student should have computer access to the internet,
to obtain assignments, submit homeworks and projects, etc.
(NOTE:
If you have ANY difficulty at all in obtaining internet access between classes
please see the instructor after class to remedy this difficulty.)
Between classes, the student should have computer access to the internet,
to obtain assignments, submit homeworks and projects, etc.
(NOTE:
If you have ANY difficulty at all in obtaining internet access between classes
please see the instructor after class to remedy this difficulty.)
 "The college expects that each student will exercise personal
responsibility with regard to class attendance. All students are
expected to attend every class session of each course for which they
are registered. Students are responsible for all that transpires in
class whether or not they are in attendance."
"The college expects that each student will exercise personal
responsibility with regard to class attendance. All students are
expected to attend every class session of each course for which they
are registered. Students are responsible for all that transpires in
class whether or not they are in attendance."
